Table of Contents
The Problem
One of the biggest challenges for sysadmins and the security team is the open share and sharing permission, where domain users have full Read/Write/Delete Access to a folder in the server. I am not talking about the Home Folder or Roaming Profile. I am talking about folders created for temporary use and got forgotten or a misconfigured ACL for a folder in an application.
The question is, How to confirm if domain users can Access/Read/Write/Delete files in a shared folder without manually reviewing the ACL for both share and NTFS in all the servers ?!
To address this issue, I created a Powershell script that will do the following:
Download and Usage
You can download the Test Sharing Permission PowerShell Script from my Github repo
The test permission script accepts the following parameters:
- [Bool] ImpersonateToWrite: PowerShell uses the provided credential to test Read/Write/Delete action aginst the folders.
- [String]PathToWrite: The directory to export the results to.
**NOTE**: The script won’t remove any file from your environment, instead, and while testing it will create a temp file and remove it to check the permissions.
.\Get-AllShare.ps1 -ImpersonateToWrite $true -PathToWrite C:\myresult.csv #for a full result and full test
.\Get-AllShare.ps1 -ImpersonateToWrite $false -PathToWrite C:\myresult.csv # For getting only the share without the (Access,Read,Write,Delete test)Result

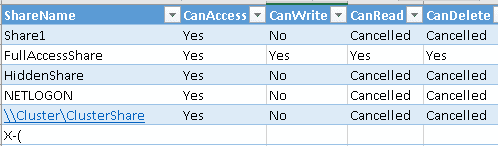
The Sharing Permission Script in Action
- Get a list of all AD Computer Server OS in Active Directory.
- Test computer connectivity.
- Read the share list and shaing permission. The share list only includes the Non-Administrative Share Folders. Admin Share such as Admin$, C$, IPC$ …, excluding printers.
- The script can read cluster share. Cluster shares are treated differently.
- If the ImpersonateToWrite parameter is set to $true, then the script requests to use another user credentials to perform Access, Write, Read, Delete on each share. Make sure that these credentials are for a limited domain user.
- Create a PSDrive and assign any available letter to the drive, this will use any available letter. At least make sure that you have 1 available letter 🙂
- If the Map was successful, then the users have the Access right. In the report, the Access is marked as Yes, else, the Write/ Delete permission test will be skipped for the folder being scanned as I assume that if the user doesn’t have the right to access a folder so this user won’t have written, read or delete access permissions.
- Then the script proceeds in Writing a file to the destination as PSCTestPSWrite.txt.
- If The Write was successful, the script will proceed in Reading it.
- The last step is to remove the created file, and the result will be updated
The script will not remove random files, it will only try to remove the file it wrote as part of the test.
Limitation of Sharing Permission Script
- The script may report that the user has full access (Access, Read, Write, Delete) in a folder where Creator Owner has full control, such as Folder Redirection, Home Folder…etc.
- There might be a duplicated result when the file server cluster has muti-rules.
You can help me in making the script better by sharing your ideas and issues in the comment or on my GitHub repo
What Else to read
You may love how PowerShell can control Windows Defender Antivirus, check it out